While the global industry has been awash with news over the Dark Side ransomware attacks on the Colonial Pipeline network in the past three weeks, the broader and more alarming development is spurt in the frequency and number of attacks since the beginning of this year.
Over March and April, we saw 56 major cyber attacks on major companies globally. The ransomware attack on Taiwan’s computer maker Acer became the largest ransom demand in history at $50 million, with the attackers sharing exfiltrated data on their leak site as proof of the attack.
Ransomware attacks also halted production at IoT manufacturer Sierra Wireless, beer maker Molson Coors and Taiwanese notebook manufacturer Quanta Computer.
Ransomware is becoming the easiest way for cyber criminals to make a lot of money by hacking networks. Many companies are forced to pay the ransom because it is the quickest means of stopping the disruption to their business.
Rising ransoms have also helped evolve ransomware from what in the past was a basic scam run by petty criminals into well-heeled professional criminal organisations with deep benches of top cybersecurity talent.
The emergence of ransomware threats began in 2013 with CryptoLocker being the first to be successfully used. Today groups like Maze, Ragnar Locker, Ryuk, Egregor, Conti and Dark Side are ruthless, well-funded and willing to target any organisation from retail to banking and government.
To date, the damage caused by ransomware in 2021 has already exceeded the results from advanced persistent threats (APT). While both attackers access the online resources from companies using administrator rights and software vulnerabilities to steal information, ransomware attacks are more insidious as they can take out the entire infrastructure and disrupt and stop business processes, just as the Colonial Pipeline attack grievously illustrates.
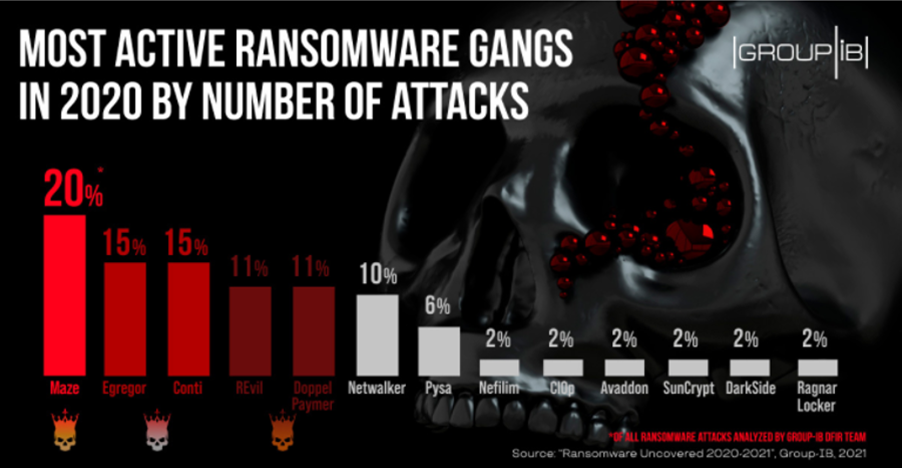
Maze was responsible for 20% of ransomware attacks in 2020.
Losses that keep mounting
Last week, we ran an opinion by Check Point on ransomware attackers upping their game through ‘double extortion’ methods.
‘Double extortion’ is now rife with the Acer attack being one example. Check Point estimated that ransomware cost businesses worldwide around US$20 billion in 2020, a figure that is a staggering 75% higher than the previous year.
Since April, researchers at Check Point Research (CPR) have seen an average of over 1,000 organisations being impacted by ransomware every week. This follows significant increases in the number of impacted organisations so far in 2021 – 21% in the first trimester of the year and 7% since April so far. These increases have resulted in a staggering 102% overall increase in the number of organisations affected by ransomware compared to the beginning of 2020.
The uncertainty of mobile working and the acceleration of digital transformation initiatives are opening doors for cyber criminals to conduct more aggressive attacks.
Similarly, in SonicWall’s 2021 Cyber Threat report, the company’s CEO Bill Conner said the pandemic — along with remote work, a charged political climate, record prices of cryptocurrency, and threat actors weaponising cloud storage and tools — drove the effectiveness and volume of cyber attacks to new highs.
“Technology is moving at an unprecedented rate. Threats that were once thought to be two or three years away are now a reality, with do-it-yourself, cloud-based tools creating an army of cybercriminals armed with the same devastating force and impact of a nation-state or larger criminal enterprise,” says Conner.
The picture is equally grim in APAC
Across the Asia Pacific, CPR said APAC organisations currently experiences the highest volume of ransomware attacks. On average, they are attacked 51 times per week. This is a 14% increase compared to the beginning of this year. Comparatively, a North American organisation experiences 29 weekly attacks, European and Latin American companies 14 and African companies each have four weekly attacks per organisation.
Ransomware attackers, explained CPR, are focusing their efforts across all industries globally. While in North America healthcare organisations have suffered the most attacks since the beginning of the year, in Europe utilities ‘organisations absorb the most attacks. In APAC, insurance/legal are most impacted, followed by manufacturing.
Globally, India has seen the most number of attacks attempts per organisation, with an average of 213 weekly attacks since the beginning of the year.
Checkpoint added that while not all incidents – and their results – are disclosed and published, statistics collected during 2020-2021 reflect the prominence of the attack vector, with the average ransom payment growing by 171% in the last year to reach about $310,000.
Threats that were once thought to be two or three years away are now a reality, with do-it-yourself, cloud-based tools creating an army of cybercriminals armed with the same devastating force and impact of a nation-state or larger criminal enterprise.
- Bill Conner, CEO at SonicWall
Over 1,000 companies suffered data leakage after refusing to meet ransom demands in 2020, and about 40% of all newly discovered ransomware families incorporated data infiltration into their attack process.
“The numbers reflect a golden attack technique, which combines both, a data breach and a ransomware threat, it is clear that attackers are still seeking methods to improve their ransom payment statistics, and their threat efficiency,” said Check Point in a recent report.
What should your organisation do?
Paul Webber, a senior director and analysts at Gartner, said that Ransomware can escalate from an issue to a crisis in no time and to counter this, organisations need to focus on preparation and mitigation to cut losses.
“Establish processes and compliance procedures that involve key decision makers in the organisation, even before preparing for the technical response to a ransomware attack.”
Webber’s advice for corporates is to do regular testing of incident response scenarios into your organisation’s ransomware response plan as well as to always maintain frequent and reliable backup and recovery capabilities.
He said another safeguard is to restrict permissions and deny non-approved employees unauthorised access to devices.
"You can also remove local administrator rights from end users and block application installation by standard users, replacing this with a centrally managed software distribution facility," says Webber.
“Use cyber crisis simulation tools for mock drills and training that provide closer to real-life situations for better preparedness of end users against ransomware.
“The challenges of ransomware and other forms of malware are the ever-changing tactics and agendas of hackers. Having a strategy in place for preparedness can help contain the losses and protect your organisation.”









