In today’s hybrid work environment, businesses face a broad and varied threat landscape as they grapple with deploying and securing remote environments while deterring ever-more opportunistic cybercriminals, emboldened by a year and a half of disruption and uncertainty.
Today, we see numerous attack methods focused on users in relatively new working conditions across a much larger attack surface. People are unquestionably the new perimeter and, in some instances, the last line of defence against a heightened combination of advanced threats, data loss, and compliance risks.
Proofpoint’s 2021 Voice of the CISO study found that almost half – 44% – of surveyed CISOs in Singapore feel at risk of suffering a material cyberattack in the next 12 months. Yet, organisational cyber preparedness remains a major concern – more than a year into a pandemic that has permanently reshaped the threat landscape, 53% of Singapore’s CISOs still feel that their organisation is unprepared to cope with a targeted cyberattack.
When it comes to bolstering cyber security, the instinct is often to protect the organisation’s top executives, the Very Important People (VIPs). However, organisations that continue to focus on protecting VIPs may be missing the forest for the trees. Individuals who are most often targeted by cyber criminals need not be top execs.
We are increasingly finding that threat actors are taking a highly strategic approach to how they target individuals in an organisation. They do their research, reviewing organisation charts and how the business operates. Sometimes this means they know their targeted firm better than its own security team does.
While all employees can fall victim to external attacks on an organisation – some are more attractive targets than others. These more targeted employees are who we call VAPs (Very Attacked People), and they are rarely the firm’s most senior executives. They tend to be employees with access to sensitive information or able to perform wire transfers at an organisation.
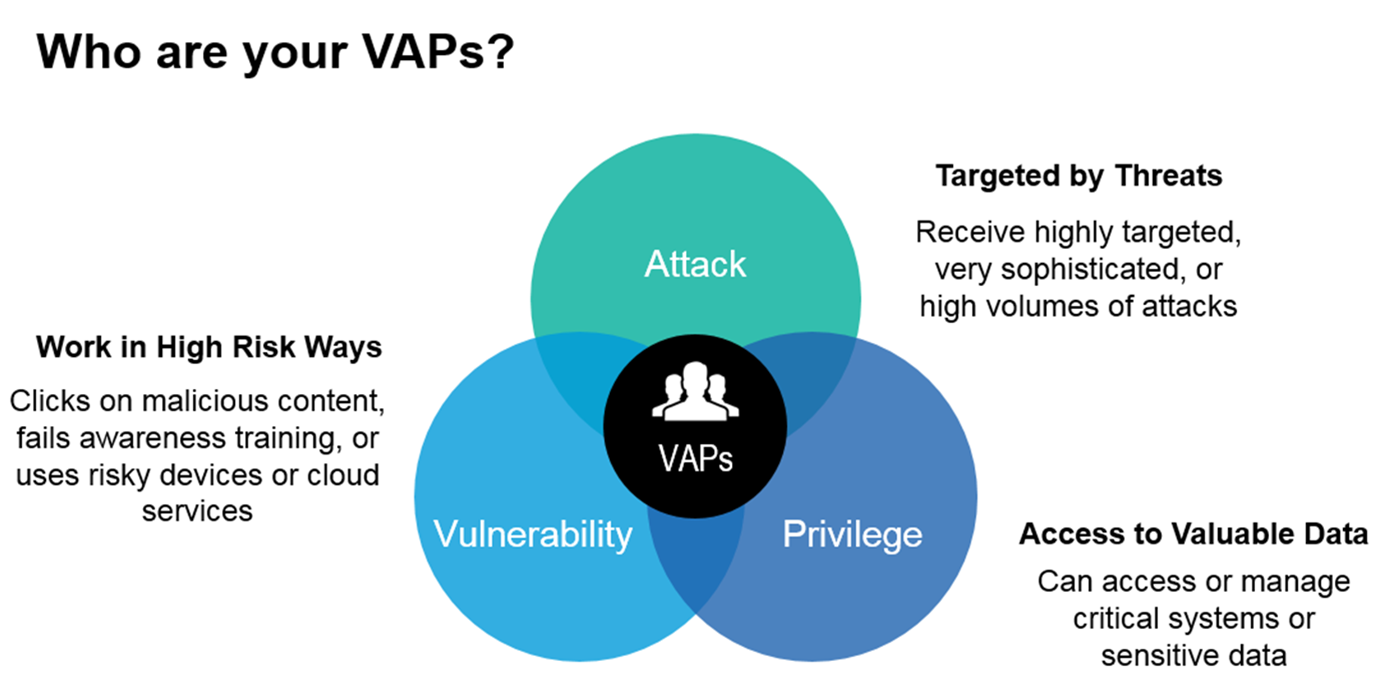
Identifying an organisation’s VAPs can be done by leveraging mathematical concepts to examine the severity and scale of cyber threats faced, as well as other data points such as what sort of URLs users are clicking on and how well they perform in phishing simulations. Machine learning and multi-layered detection techniques are also critical in identifying and dynamically classify today’s threats including imposter email, phishing, malware, spam, bulk mail and more.
Crunching these numbers provides us with a view of who the VAPs in a firm are and provides a distinct advantage over attackers as we can now prioritise our efforts to secure users the same way attackers are prioritising theirs. Training can then be tailored to address specific threats and job roles, address threats with greater certainty, and continually monitor the skill level of those on the front line.
A security-conscious culture can protect your VAPs
The concept of VAPs underscores the importance of the human factor in cybersecurity, and it needs to be a key pillar of an organisation’s cybersecurity defences. In fact, 37% of CISOs in Singapore consider human error to be their organisation's biggest cyber vulnerability. Purposefully leaking data (criminal insider attack), falling victim to phishing emails and clicking malicious links or downloading compromised files were cited as the most likely ways employees put their business at risk.
Organisations need to create a security-conscious culture where each and every employee within the organisation is aware of the role they play in practising good security hygiene. Organisations that fail to create a culture of cyber awareness and responsibility will always be the most vulnerable to attack.
Armed with the knowledge of who the enterprise’s VAPs are, they can then take steps to spot and close security knowledge gaps. To increase user understanding of complex cybersecurity topics and bring about a change in behaviour, the only effective plan of action is comprehensive, ongoing training, that keeps pace with the cyberthreats organisations are facing.
The good news is, Singaporean CISOs are already prioritising improving employee security awareness and investing in new solutions to address the shift to widespread remote working arrangements.

Threat actors are taking a highly strategic approach to how they target individuals in an organisation. They do their research, reviewing organisation charts and how the business operates. Sometimes this means they know their targeted firm better than its own security team does.
-Alex Lei, Senior Vice President, APJ at Proofpoint.
The human factor is a line of defence that is usually overlooked, and the key considerations for strengthening cybersecurity training should include:
- Ensuring comprehensive and continuous cybersecurity training for all employees, at all levels. This means not only training and refreshing end users on how to spot a phishing attack, but what to do when they occur and also eradicating any behaviour that can impact the security of your business.
- Treat traditional phishing attacks with the importance they deserve. Ensure that users know how to spot them and what to do if and when they occur. But know that to stand a greater chance of preventing such attacks, security training must extend far beyond this.
- Educating employees on the “why” as well as the “what”. Not just what a threat looks like but how it works, the motivation behind it and the ways that their behaviour can increase its success rate. That’s true not just of phishing, but of every security challenge faced by end users.
When awareness and understanding increases, behaviour changes. And that might just be the difference between a successful attempt and a successful attack.
Cyber theme moving towards high risk, high reward
Amidst the fast-evolving threat landscape, high risk, high reward is expected to be a common cyber theme over the next two years. Our study found that almost half – 48% – of CISOs in Singapore believe that cyber crime will become even more profitable for attackers, while 41% believe that it will become riskier for cyber criminals.
Security is a shared responsibility. Organisations must empower employees at all levels to understand security and the risky behaviours that can lead to breaches. Training and awareness programs are crucial, but one size does not fit all. Make sure your program is from the perspective of the user – make it relevant to their work and personal lives.
Companies must also bring people into our security fold. Provide simple ways for users to report back to the security team. For example, single click buttons that automatically send potential phishing emails to the security team to analyse – in this case, false positives are a good problem to have.
Over 99% of cyber threats require human interaction to be successful. When your people are that vital to an attack, they need to be a vital part of your defence. Cyber criminals spend day and night trying to penetrate your networks, systems, and data. The least we can do is make them work a little harder.
Alex Lei is Senior Vice President, APJ at Proofpoint.









