Security researchers have found a new exploit that allows attackers to remotely execute code through Outlook Web Access (OWA), on Microsoft Exchange Server.
Crowdstrike said the new exploit method uses two vulnerabilities, and bypasses the URL or link rewrite mitigations for the ProxyNotShell bug that Microsoft provided and which affect on-premises Exchange servers.
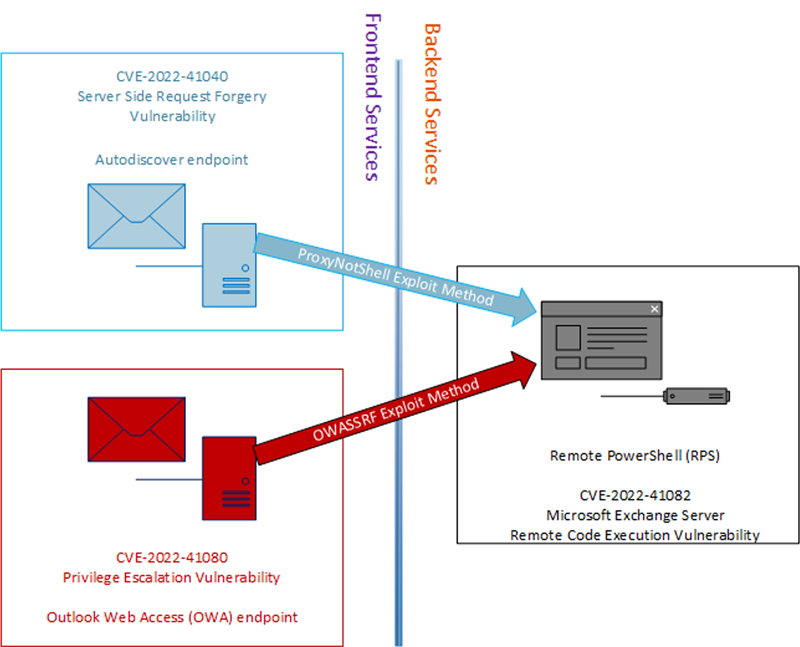
The security vendor called the exploit method OWASSRF, or Outlook Web Access Server-Side Request Forgery.
First, the Autodiscover endpoint, used for informing clients about services offered by the remote Microsoft Exchange server, is accessed using an authenticated request to the frontend, Crowdstrike researchers said.
It is accessed using a path confusion exploit, CVE-2022-41040, allowing the attacker to reach the backend for arbitrary URLs.
This type of vulnerability is known as a server-side request forgery (SSRF).
In the case of ProxyNotShell, the targeted backend service is the Remote PowerShell service.
A proof-of-concept link leading to leaked code for the new exploit was posted to Twitter by Huntresslabs security researcher Dray Agha.
Agha had found the attackers' toolkit in an open repository and downloaded them all.
By using a Python script posted by Agha, Crowdstrike was able to replicate the log file entries in recent attacks.
Crowdstrike discovered the ProxyNotShell mitigation bypass when the security firm investigated Play ransomware intrusions, with the common entry vector being Microsoft Exchange.
Exchange Server is a common target for hackers, with several exploit and attacks recorded in recent times.
A high profile attack on Rackspace took out the cloud providers hosted Exchange Service, with customers told to migrate to Microsoft 365 as mitigation.
Some days later, Rackspace confirmed that the cause of the outage was a ransomware attack by unnamed miscreants, forcing the company's support technicians to enter into time-consuming data recovery processes for customers.
Rackspace said it hired Crowdstrike to assist with the investigation of the ransomware attack.
Crowdstrike said that since URL rewrite mitigations are not effective for ProxyNotShell, Exchange admins should apply Microsoft's November patches to prevent exploitation.
Admins who cannot immediately patch their Exchange servers should disable OWA as soon as possible, and follow Microsoft's recommendations to disable remote PowerShell for ordinary users where possible.