There are four key lessons we can learn from how remote working has impacted security, says Check Point Software in the release of if 2021 Remote and Hybrid Work Security Report.
The report polled 450 IT security professionals globally, half of them holding senior leadership roles (directors, VP or C-suite execs), and will have a huge bearing on organisations' security and network architectures as organisations start building hybrid workplace.
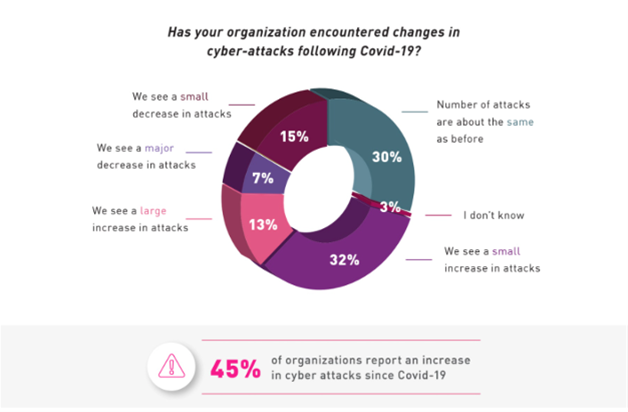
About half of global companies polled have seen cyber attacks increase
Lesson #1 - Remote work makes you more vulnerable
Almost half or 45% of all respondents have seen an increase in cyber attacks since COVID-19. The most cited types of attacks were data exfiltration and leakage (55%), phishing emails (51%) and account takeover (44%).
The report said that considering that remote working does not provide the same level of protection within and outside the corporate firewall, this is not entirely surprising. For example, when working outside the office, users may casually browse to a malicious ad or click a phishing link from a personal email; yet their internet traffic may not be inspected and blocked for malicious URLs.
By routing all traffic for security inspection, for example, through a cloud secure web gateway integrated with a cloud DLO, this extra risk can be mitigated.
Lesson #2 - Traditional solutions are strained by remote work needs
When supporting remote work, the top three administration challenges reported were scaling performance (46%), addressing privacy and data sovereignty concerns (42%) and supporting remote access for employees’ unmanaged devices (40%).
Whereas cloud-based security and networking services can alleviate congestion and improve application speed and performance, privacy and compliance concerns can be addressed by using local points of presence (PoPs).
With the emergence of service-initiated zero trust network access from the cloud, organisations can support client-less remote access from unmanaged BYOD devices, including devices used by third parties (such as partners and consultants) without the need to install or manage an agent.
Lesson #3 - Remote Worker complaints point to connectivity issues
The most common reasons for help desk tickets were performance (latency) (67%), instability and crashes (66%) and VPN issues (62%).
While connection speeds and performance can be improved with network optimisation solutions such as SD-WAN, moving from a client based to clientless remote access solution can eliminate VPN-related issues caused by VPN clients.
Lesson #4 - The pressure is on to add remote access capacity
To handle the spike in remote working, 69% of security professionals report they are adding on-prem capacity; 66% are moving to cloud-based security and surprisingly, 36% do both.
For expediency, it may be easier to add capacity to current solutions, rather than rip out and replace them with completely new ones. Alternatively, this may reflect a phased approach to adopting cloud-based services or may be a result of data residency considerations.
Of those using cloud to beef up remote access, (61%) perceive cloud-based security services as highly strategic in their overall efforts to scale secure remote user access. And already today one-third of organisations have already implemented or are planning to implement secure access service edge (SASE) services.
Is SASE a logical next step?
The spike in cyber attacks, the added complexity of ensuring privacy for remote workers and the need to know what users are actually doing, even when they connect from their own devices, may all seem to be separate issues to be tackled one by one.
Check Point says it may be time for organisations to explore how security services, such as zero-trust network access (ZTNA), secure web gateway (SWG) and branch office firewall-as-a- service (FWaas) and SD-WAN to secure growing remote and hybrid workforces.
A SASE architecture conceived for remote workers, unified and delivered from the cloud, can help connect any user or branch, from any device, to any target resource, without compromising on security.










